Updated: Jan 13, 2025
Imagine a company where every user, every device, and every connection is under continuous scrutiny, and only those with verified credentials are allowed access to specific resources. This is not Orwell’s dystopian viewpoint; it’s the cornerstone of zero trust; a cybersecurity approach that assumes no user or device can be trusted. Cisco Identity Services Engine (ISE) sits at the heart of this concept, enabling water-tight network access and redefining how enterprises secure their digital world.
The zero-trust model has become an industry standard, particularly as cyber threats evolve, and organisations embrace hybrid work environments. According to a 2024 survey by Gartner, over 60% of enterprises plan to implement zero-trust strategies by 2025. Cisco ISE, a policy-based access control platform, is a perfect solution for implementing these strategies by providing robust identity management and dynamic network segmentation.
Why is this shift critical? A single misstep in identity verification can grant attackers free access to an organisation’s crown jewels—its data. By integrating Cisco ISE, enterprises gain an invaluable ally in mitigating such risks.
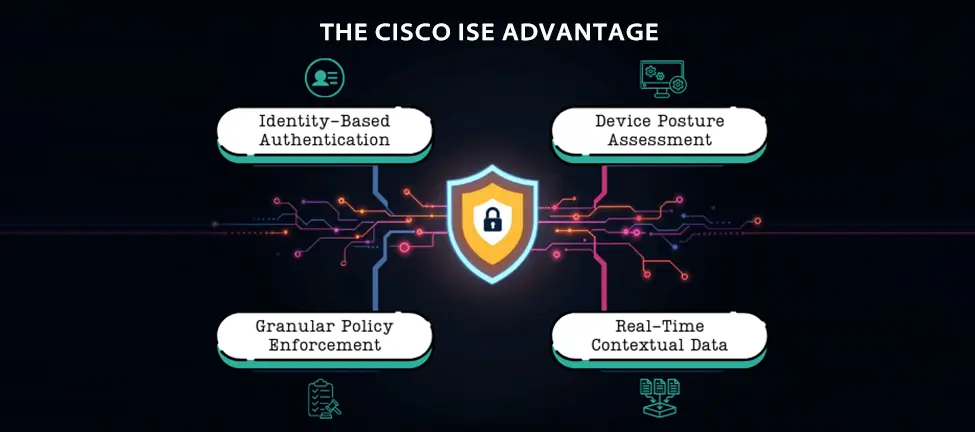
Cisco ISE goes beyond traditional network access control (NAC) by delivering context-aware access policies. This capability is vital in today’s interconnected world, where users frequently switch between devices and locations. Here’s how Cisco ISE achieves this:
Traditional perimeter-based security models falter in dynamic and hybrid environments. Cisco ISE addresses this limitation with dynamic network segmentation, enabling enterprises to create micro-perimeters within their networks. These micro-perimeters minimise lateral movement, a common attack vector in breaches.
Dynamic segmentation is particularly beneficial for securing Internet of Things (IoT) devices. According to IoT Analytics, the number of connected IoT devices is expected to surpass 17 billion by 2025. Many of these devices lack inherent security features, making them prime targets. Cisco ISE’s ability to segment IoT traffic and restrict communication to pre-approved endpoints is a game-changer.
A global financial institution deployed Cisco ISE to secure its hybrid work environment. The challenge? Ensuring seamless and secure access for 20,000 employees spread across five continents. By leveraging ISE’s context-aware policies, the institution achieved the following:
Integration with the Broader Cisco Ecosystem
Cisco ISE is not a standalone solution; it’s a critical component of Cisco’s secure networking ecosystem. Integration with technologies like Cisco Umbrella, SecureX, and Catalyst switches amplifies its capabilities. For example:
ISE Deployment: Some Common Challenges
While Cisco ISE offers unparalleled benefits, its deployment requires careful planning and expertise. Organisations often face challenges such as:
The Road Ahead: AI-Driven Enhancements
Cisco is continually evolving ISE to address future challenges. Recent updates have incorporated AI and ML capabilities, enabling predictive analytics and automated threat responses. For example, ISE’s machine learning models can identify unusual login patterns and flag potential insider threats before they erupt like a volcano.
With increasingly sophisticated cyber threats, Cisco ISE emerges as a cornerstone of secure, context-aware access. Its advanced capabilities make it an indispensable tool for CISOs, CIOs, and CTOs striving to protect their organisations. By embedding zero-trust principles at the core of network security, Cisco ISE ensures that trust is earned—never assumed.
At Proactive Data Systems, we specialise in deploying and optimizing Cisco ISE to align with your unique business needs. Let us help you transform your network security, protect critical assets, and build a future-ready, zero-trust framework. Contact us today to explore how our expertise can safeguard your organisation.
References